

How RDPExtra Delivers RDP DDoS Protection for RDP Servers
Remote Desktop Protocol is the backbone of modern remote work, automation, and server management. But as RDP usage grows, so do attacks targeting exposed servers. Among them, DDoS attacks are the most damaging and least forgiving.This guide explains how RDP DDoS protection works in real hosting environments and how RDPExtra secures RDP servers against attacks.As a result, businesses that rely on RDP uptime need protection that works automatically without manual intervention.
At RDP Extra, secure RDP hosting is not a marketing line. It is an operational requirement. This case-study-style guide explains how RDP Extra delivers RDP DDoS protection, what threats actually look like in real environments, and why price-sensitive buyers can still get serious protection without paying enterprise-only rates.
We will also break down plan-level protections, show a clear comparison table, and explain what makes RDP Extra a safer choice for long-term RDP use.
Understanding RDP-Based DDoS Attacks


Remote Desktop runs on Windows systems using TCP 3389 and, in many setups, UDP 3389. While UDP improves session speed, it can also be abused if left exposed.
Attackers exploit misconfigured RDP servers to perform reflection and amplification attacks. Small forged requests generate large responses, flooding the target with traffic. In real cases, amplification ratios can exceed 80:1.
These attacks do not just hit websites. They disrupt RDP access, overload network links, exhaust firewall state tables, and cause random disconnects that users often mistake for “server issues.”
For businesses that rely on RDP uptime, the impact is immediate and costly.
Why Traditional RDP Hosting Fails Under DDoS
Many low-cost RDP providers focus only on CPU, RAM, and disk. Security is treated as an optional extra.
This creates predictable problems:
- Open UDP 3389 ports exposed to the internet
- No upstream traffic filtering
- Shared mitigation pools with slow response
- One-size-fits-all firewall rules
When attacks happen, users face downtime or forced suspensions.
RDP attack mitigation must be built into the hosting layer itself. That is where RDPExtra takes a different approach.
RDP Extra’s Security-First Hosting Architecture
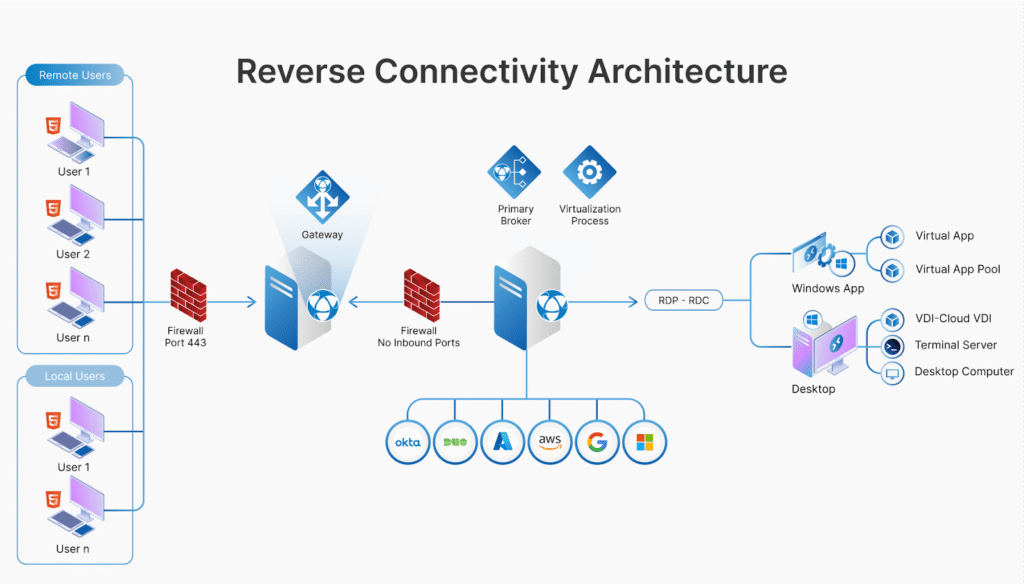

RDP Extra designs its infrastructure with DDoS defense for VPS environments from day one.
Instead of reacting after an attack starts, traffic is filtered, shaped, and verified before it reaches the RDP server. This reduces collateral damage and keeps legitimate sessions stable.
Key architectural principles include:
- Controlled exposure of RDP services
- Layered traffic inspection
- Intelligent rate limiting
- Segmented customer environments
This approach allows RDP Extra to deliver strong protection without raising prices beyond reach for everyday users.
How RDP Extra Mitigates RDP DDoS Attacks
1. Controlled RDP Port Exposure
RDP Extra minimizes public exposure of UDP-based RDP where it is not required. When UDP is enabled, it is tightly monitored and rate-limited.
This alone removes the most common amplification abuse pattern.
2. Upstream Traffic Filtering
Before traffic reaches the server, volumetric floods are filtered at the network edge. This prevents saturation of bandwidth and avoids firewall exhaustion.
3. Intelligent Rate Limiting
Abnormal request patterns are throttled automatically. Legitimate RDP sessions continue without interruption, even during active attack windows.
4. Network Segmentation
Each RDP instance operates in an isolated environment. An attack against one customer does not spill over to others.
5. Continuous Monitoring
Traffic patterns are monitored 24/7. Sudden spikes trigger automatic mitigation without waiting for manual intervention.
Together, these measures form a complete RDP DDoS protection stack rather than a single point solution.
Real-World Impact: A Practical Case Study
One of RDP Extra’s automation users experienced repeated UDP floods targeting their exposed RDP port. Previous hosting setups failed within minutes.
After migrating to RDP Extra:
- Attacks were absorbed upstream
- No RDP session drops occurred
- CPU and memory usage remained stable
- Automation tasks continued uninterrupted
This is the difference between reactive hosting and secure RDP hosting designed for real threats.
RDP Extra Security Features That Matter

RDP Extra focuses on features that actually reduce risk, not checkbox security.
Core RDP security features include:
- Hardened Windows configurations
- Pre-configured firewall rules
- Optional VPN-based RDP access
- Automated abuse detection
- Fast incident response
These features protect both performance and reputation, which is critical for SEO, automation, and business continuity users.
RDP Extra vs Standard RDP Hosting (Feature Comparison)
| Feature | Standard RDP Hosting | RDPExtra Secure RDP |
| RDP DDoS protection | Limited or none | Built-in, always on |
| UDP 3389 control | Open by default | Strictly managed |
| Upstream filtering | No | Yes |
| Network isolation | Shared | Isolated |
| DDoS defence for VPS | Basic | Advanced |
| Monitoring | Reactive | Proactive |
| Price accessibility | Low | Low to mid |
| Downtime during attack | Likely | Rare |
This comparison highlights why cheap RDP without protection becomes expensive in the long run.
Pricing-Focused Plans With Built-In Protection
Price-sensitive buyers often assume security equals high cost. RDP Extra proves otherwise.
Sample RDP Extra Plan Structure
| Plan Type | Best For | DDoS Protection | Starting Price |
| Entry RDP | Light usage | Basic filtering | Affordable |
| Standard RDP | SEO, automation | Full mitigation | Mid-range |
| Advanced RDP | High uptime needs | Priority protection | Value-focused |
Every plan includes baseline RDP attack mitigation, with higher tiers adding more aggressive filtering and monitoring.
No hidden security add-ons. No surprise charges during attacks.
Why VPN-Backed RDP Access Matters
Exposing RDP directly to the internet increases risk. RDP Extra supports VPN-based access models that hide RDP services from public scanning.
This significantly reduces:
- Reflection abuse
- Brute-force attempts
- Automated bot attacks
For users running mission-critical workloads, VPN access adds an extra layer of confidence without complexity.
Compliance With Industry Best Practices
RDPExtra follows widely accepted network and operational best practices used by large infrastructure providers and mitigation specialists such as NETSCOUT Arbor.
This includes:
- Periodic security testing
- Controlled protocol exposure
- Layered mitigation strategies
- Ongoing tuning based on attack trends
Security is treated as a process, not a one-time setup.
Who Should Choose RDP Extra for Secure RDP Hosting
RDP Extra is ideal for:
- SEO professionals running automation
- Agencies managing multiple sessions
- Developers hosting applications
- Remote teams needing stable access
- Budget-focused users who still want protection
If uptime matters and downtime costs money, secure RDP hosting is not optional.
Final Thoughts: Security Without Overpricing
DDoS attacks on RDP servers are not theoretical. They are active, automated, and increasing every year.
RDP Extra addresses this reality with practical RDP attack mitigation, transparent pricing, and infrastructure designed for uptime. You do not need enterprise budgets to get serious protection.
If you want reliable, secure RDP hosting that stays online when attacks happen, RDP Extra delivers value where it actually matters.
👉 Explore RDP Extra plans today and protect your RDP before the next attack starts.
Frequently Asked Questions
Yes. All RDPExtra plans include baseline RDP DDoS protection. Higher plans offer stronger filtering and faster response, but no plan is left unprotected.
Large attacks may increase latency briefly, but RDPExtra’s upstream mitigation prevents full outages and session drops in most cases.
No. Security features are pre-configured. You use your RDP normally without managing firewalls or mitigation rules.
Not with RDPExtra. Plans are priced for everyday users while still including real DDoS defence for VPS environments.
