11 Best Practices to Secure Remote Desktop Access
Secure remote desktop access has become a critical requirement for modern businesses. What started as a convenience tool has now evolved into an essential part of daily operations for IT teams, remote employees, agencies, and service providers. The shift toward remote and hybrid work environments accelerated this adoption, and even after that period, remote desktop access continues to play a central role in how organisations operate.
With this widespread usage, however, came a sharp increase in cyberattacks targeting remote desktop connections. Attackers actively look for exposed RDP ports, weak credentials, outdated systems, and misconfigured security settings. In many real-world incidents, a single overlooked configuration has been enough to allow ransomware deployment or unauthorised access to sensitive systems.
In this blog, we will explore the most common risks associated with remote desktop access and walk through proven best practices that help organisations maintain secure remote desktop access without sacrificing productivity or flexibility.
What Is Remote Desktop Protocol (RDP)?
Remote desktop access refers to the ability to connect to and control a computer or server from a different location. On Windows-based systems, Remote Desktop Protocol (RDP) enables this functionality.
RDP is a Microsoft-developed protocol that allows users to interact with a remote system using a full graphical interface. Unlike command-line-based access methods, RDP enables users to work on a remote machine using their local keyboard, mouse, and display, creating an experience similar to sitting directly in front of that system.
RDP handles the transmission of screen visuals, keyboard inputs, mouse movements, and session data between the local and remote devices. Because of this, it is widely used for server administration, technical support, automation workflows, and virtual machine management. Its power and convenience also make it a frequent target for attackers when security controls are weak or incomplete.
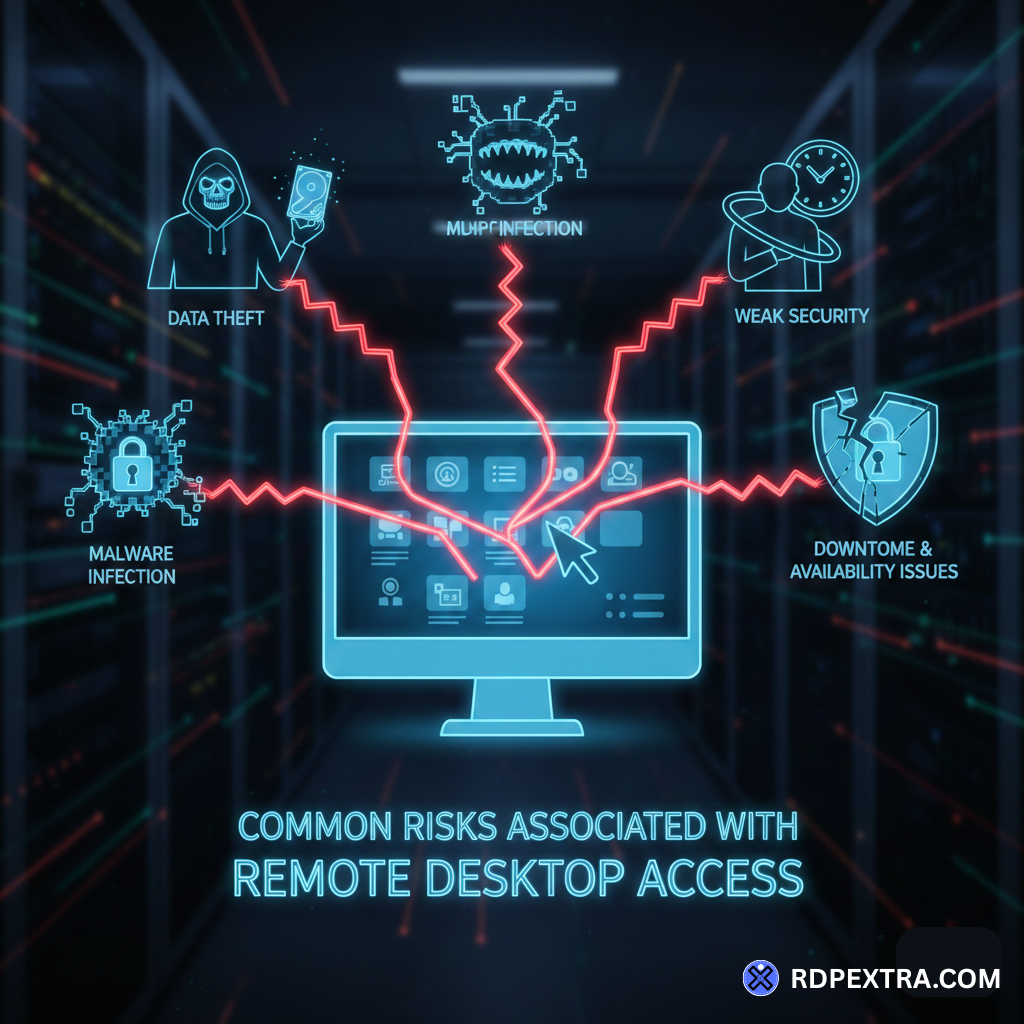
Common Risks Associated with Remote Desktop Access
Understanding the risks is the first step toward building secure remote desktop access and support systems.
Brute-Force Login Attacks
Attackers frequently target RDP by attempting repeated login combinations until valid credentials are discovered. Weak, reused, or predictable passwords significantly increase the success rate of these attacks and can lead to complete system compromise.
Unpatched or Outdated RDP Systems
Systems that are not regularly updated are often vulnerable to known exploits. Attackers continuously scan for outdated RDP servers that can be compromised using publicly available attack tools.
Weak or Misconfigured Remote Desktop Encryption
Modern RDP sessions support strong encryption by default, but misconfigurations or legacy settings can weaken remote desktop encryption. This may expose login credentials or session data to interception.
Ransomware and Malware Deployment
Unsecured RDP connections remain one of the most common entry points for ransomware attacks. Once access is gained, attackers can deploy malware, encrypt critical data, disable backups, and move laterally across networks.
Excessive Access and Permissions
Allowing too many users or granting administrative privileges unnecessarily increases risk. A single compromised account with elevated access can lead to widespread damage.
Abuse of Remote Management Capabilities
After gaining RDP access, attackers often leverage built-in tools to execute commands, change permissions, and escalate privileges across connected systems.
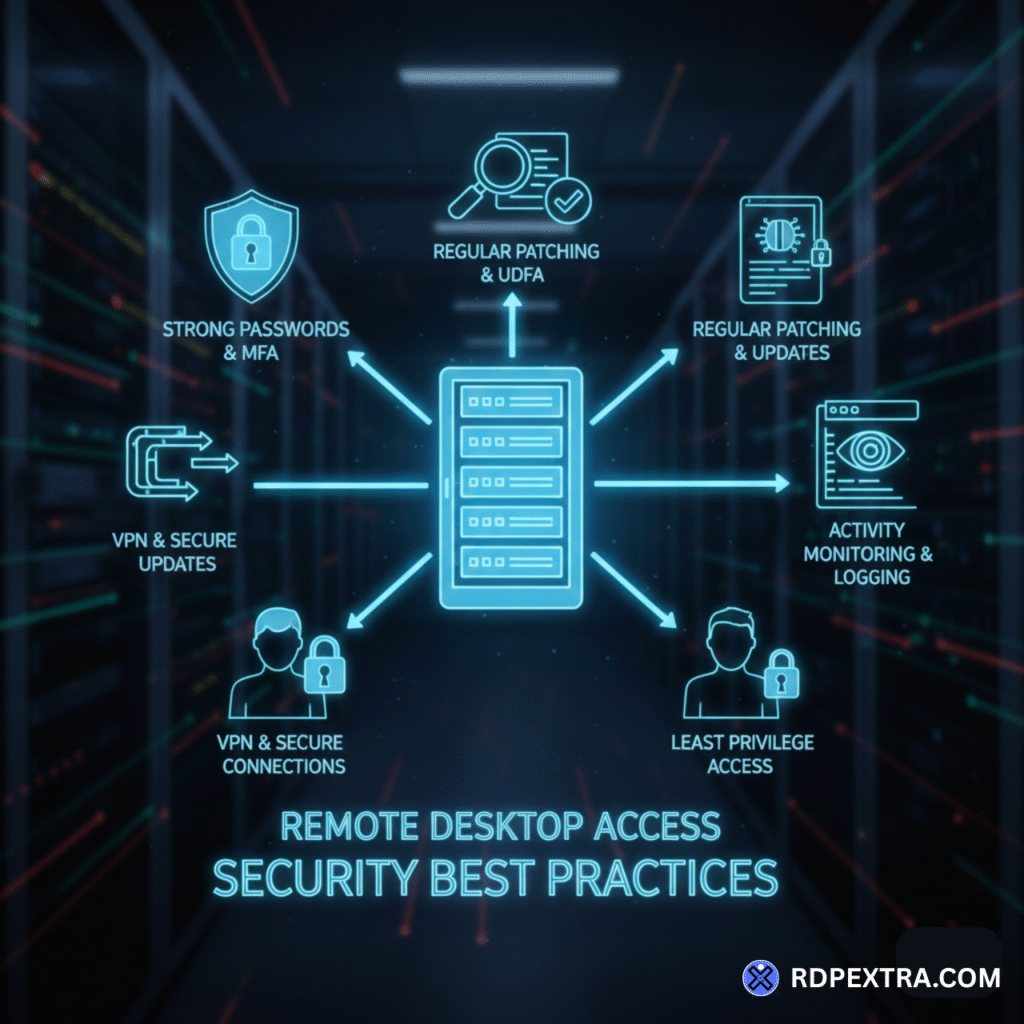
Remote Desktop Access Security Best Practices
The following best practices focus on strengthening secure remote desktop access while maintaining usability and performance.
1. Use Multi-Factor Authentication (MFA)
Passwords alone are no longer sufficient to protect remote desktop environments. Even strong passwords can be stolen through phishing, malware, or credential reuse. This is why RDP MFA is one of the most important security controls you can implement.
Multi-Factor Authentication adds a verification step, such as a mobile authenticator prompt, hardware security key, or one-time passcode. Even if credentials are compromised, attackers cannot access the system without the second factor.
For organisations managing multiple users, MFA policies can also be applied based on device trust, login location, or risk level, providing both security and flexibility.
2. Avoid Exposing RDP Directly to the Internet
One of the most critical rules of secure remote desktop access is to never expose the RDP service directly to the public internet. Open RDP ports are constantly scanned by attackers and automated bots.
Instead, RDP access should always be routed through a secure access layer such as a private network connection, secure gateway, or protected internal environment. This ensures that users must authenticate through a trusted channel before an RDP session is even possible.
3. Enable RDP Network Level Authentication
RDP Network Level Authentication is a security feature that requires users to authenticate before a full remote desktop session is established. This significantly reduces the attack surface.
When Network Level Authentication is enabled, unauthorised users are blocked early in the connection process, preventing unnecessary system resource usage and reducing exposure to denial-of-service attempts. Enforcing RDP network-level authentication across all systems is a foundational security step.
4. Use Firewalls and IP-Based Restrictions
Firewalls act as the first line of defence for remote desktop environments. Rather than allowing RDP connections from any location, restrict access to known IP addresses, VPN ranges, or internal networks.
Both network-level firewalls and host-based firewall rules should be configured to limit who can initiate RDP connections. This layered approach dramatically reduces the likelihood of unauthorised access attempts.
5. Apply the Principle of Least Privilege
Not every user requires remote desktop access, and even fewer require administrative privileges. Applying the principle of least privilege ensures that users receive only the permissions necessary to perform their specific tasks.
Regularly reviewing RDP access permissions helps identify outdated accounts, excessive privileges, and unnecessary access. Reducing access scope limits the impact of compromised credentials.
6. Consider Secure Cloud-Based Remote Desktop Environments
Managing traditional RDP infrastructure requires constant monitoring, patching, and configuration. Secure cloud-based remote desktop environments reduce this operational burden by offering built-in security controls, managed updates, and centralised access management.
These environments often eliminate the need for public-facing RDP endpoints, which significantly lowers exposure to external threats while improving scalability and reliability.
7. Configure Account Lockout Policies
Brute-force attacks depend on unlimited login attempts. Account lockout policies automatically disable accounts after a defined number of failed login attempts, effectively stopping automated attacks.
For sensitive or high-privilege accounts, stricter lockout rules provide an additional layer of protection without impacting regular users.
8. Implement RDP Session Timeout Policies
Inactive remote desktop sessions present a security risk. If a user leaves a session open, it may be accessed by unauthorised individuals.
Configuring an RDP session timeout ensures that idle sessions are automatically disconnected after a defined period of inactivity. This helps protect sensitive data and reduces the risk of unauthorised session misuse.
9. Keep Operating Systems and RDP Clients Updated
Outdated systems are among the easiest targets for attackers. Security updates often patch vulnerabilities that are actively exploited in real-world attacks.
Regularly updating operating systems and RDP clients helps protect against known exploits and ensures that remote desktop encryption and security features remain effective.
10. Monitor and Audit Remote Desktop Activity
Visibility is essential for maintaining secure remote desktop access and support. System logs provide valuable insight into login attempts, session durations, and connection patterns.
Regularly reviewing these logs helps detect suspicious behaviour such as repeated failed logins, unexpected access times, or connections from unfamiliar locations. Early detection allows organisations to respond before serious damage occurs.
11. Educate Users on Secure Remote Access Practices
Technology alone cannot fully secure remote desktop environments. Users play a critical role in maintaining security.
Security awareness training should cover safe credential handling, recognising phishing attempts, verifying connection destinations, and properly ending remote sessions. Educated users help reinforce technical controls and reduce human-related risks.
Closing Thoughts
Securing remote desktop access is an ongoing process, not a one-time configuration. Threats continue to evolve, and security measures must evolve with them.
Each best practice outlined above addresses a specific vulnerability. When combined, they create multiple layers of defence that significantly strengthen secure remote desktop access and support. If one control fails, others remain in place to reduce risk.
Start by reviewing your current remote desktop setup against these recommendations, prioritise improvements based on risk, and implement changes systematically. A well-secured remote desktop environment is essential for stability, trust, and long-term operational success.
Thanks for reading. We hope this guide helps you build a safer and more reliable remote desktop environment.
Frequently Asked Questions About Secure Remote Desktop Access
Secure remote desktop access refers to connecting to a remote system using strong security controls such as encryption, authentication, and access restrictions. It ensures that only authorised users can access remote desktops while protecting sensitive data from unauthorised access, cyberattacks, and credential misuse.
RDP MFA adds an extra layer of protection by requiring users to verify their identity beyond a password. Even if credentials are stolen, attackers cannot access the system without the second factor, making RDP MFA one of the most effective ways to prevent unauthorised remote desktop access.
RDP network-level authentication requires users to authenticate before a remote desktop session is created. This blocks unauthorised connection attempts early, reduces server resource usage, and limits exposure to brute-force and denial-of-service attacks, significantly improving overall remote desktop security.
An RDP session timeout automatically disconnects inactive remote desktop sessions after a defined period. This prevents unauthorised access to unattended systems, protects sensitive data, and reduces security risks caused by forgotten or idle sessions in shared or business environments.